| |
Roles and all could wait, though; the first task was to come up with some
means of bringing in new users, setting their nicknames based on information
from their "badgename" at the Registration site, and applying the "Arisian"
role which would unlock the rest of the site for them.
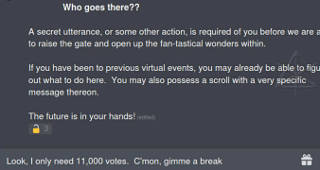
Gail had spoken of having the online site generate a unique string, along
with instructions to copy and paste it into some suitably "magic" area
of Discord, as a possible strategy.
Or, the inverse.
It wasn't even clear which way the information had to flow, but the
bottom line was that there was no automatic way to tie people with their own
independent Discord accounts to their Arisia presence, without some means
for them to simply tell us about it.
We weren't going to force anyone to create a new account just for this.
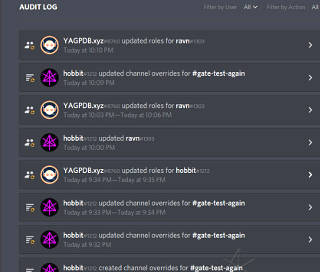
So some snippet of data would have to be "manually" carried between Discord
and the Arisia backend, and databases suitably updated.
The backend wasn't my problem but I figured I could take something generated
from there, and use it to perform the necessary functions on the Discord side.
See the Rathole: Discord API innards section later in
the main flow for more on what we ultimately ran with.
Fortunately I already had been working on this sort of thing, and had a
couple of successful experiments in parsing ordinary message typein to a
channel and taking actions based on it.
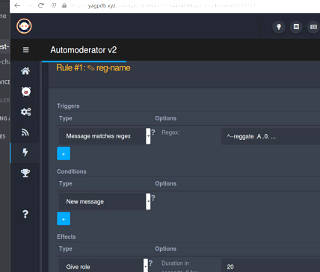
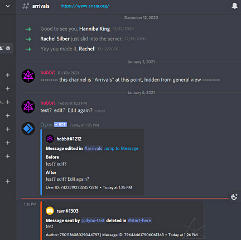
A big part of most "bot" functionality is auto-moderation, where words and
phrases considered "bad" can trigger actions, warnings, message deletion,
user sanctions, etc.
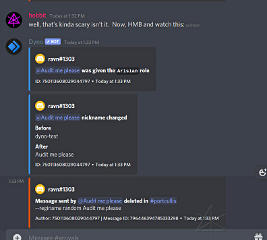
The channel-content parsing has been greatly extended in many cases,
enabling things like completely customized commands that can have the bot
run little configurable mini-programs or scripts that Do Stuff.
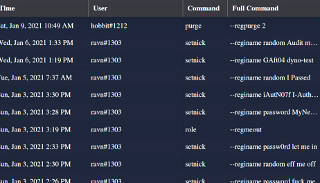
The problem I now had was arbitrary parsing of arguments and plugging
those back into another function, and the existing bot [YAGPDB, for "Yet
Another General-Purpose Discord Bot"] seemed to have fairly obscure methods
for handling that if it could at all.
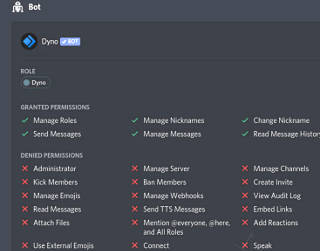
To have an easier time of it, I brought in another bot called
"Dynobot",
which has a more straightforward way to handle arguments in custom commands.
[I also looked at MEE6, and gave up on it.
Not only does it keep spamming users about junk "levels",
anything vaguely useful in it is limited by a paywall.
Eff that.]
|