|
Well, maybe not entirely...
I was still super-curious how a website was going to convince my
*not-logged-in* Zoom client to start a meeting or webinar under some user
account I didn't even know.
The launch links were buried in multiple layers of javascript, but with a
little hackery I managed to capture one of them and discovered that it
was a monster.
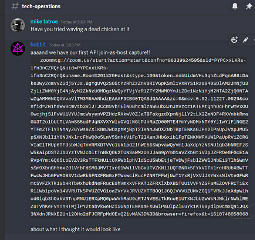
In this massive, obscenely pulsating blob were many sub-elements, and when I donned my gasmask and seriously sliced it open to the squishy innards, it turned out that some of that foul plumbing was *triple* or more base64-encoded. Here's what it looked like when laid out across the slab.
-- |
| But lo, some other netherworld horror had stirred deep within the machine, because as this night progressed, even the good-faith efforts to get sessions rolling started to go awry. The host launch links weren't showing up, or going to the wrong meeting ID, or something ... so then there was a mad scramble to generate launch links somehow and transmit them to the hosts, and frankly I wasn't fully sure what the workarounds entailed, since I was dealing more with Discord at the time. Suffice to say that #tech-ops was a bit of a disturbed hornet nest for a few hours. |